Goals
It's nice to be able to access your own services when you're on the move. The operation of a publicly accessible Nextcloud installed in the local network can be realized ingeniously simple with a Let's Encrypt certificate and HAProxy on the OPNsense firewall.
Nevertheless: Although this expansion stage is now suitable for public operation, it must be regularly updated and maintained. Nothing is worse than an outdated and therefore vulnerable installation.
Last update:
- 17.01.2026: Nextcloud 32 tested and control
- 26.03.2023: Initial document
Precondition for public operation
- Nextcloud from the first part is installed and ready.
- Own subdamain domain with fixed IP or DyDNS address is available.
- opnSense firewall with the installed plugins os-haproxy and os-acme-client.
- Important! The admin interface has been moved from port 443 to 4433.
- With the plugins os-haproxy and os-acme-client installed.
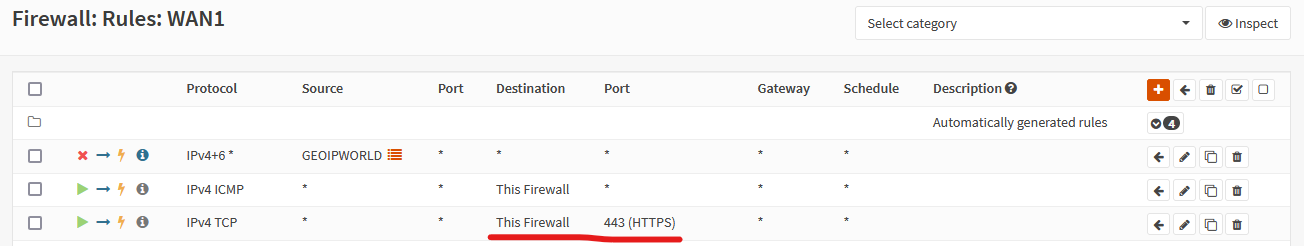
- Access to TCP port 443 is allowed on WAN.
- Internally, the EXTERALHOSTNAME should be set to the IP of the OPNsense (so that internal calls are also routed to the HAProxy).
Terminology
- EXTERALHOSTNAME = The externally accessible hostname
- ACCOUNTNAME = Name of the Let's Encrypt Account
- EMAILADDRRESS = Email Adresse of the Let's Encrypt Accounts
- NEXTCLOUDIP = IP Adresse of the local NEXTCLOUD Server
- NEXTCLOUDHOSTNAME = Hostname of the local NEXTCLOUD Server
Diagramm
With this the setup looks now like this:
┌──────────────────────┐ ┌─────────────────────────┐
│ OPNsense │ │ FreeBSD │
│ │ │ ┌─────────────────────┐ │
│ │ │ │ jails/nc │ │
WAN: 0.0.0.0:443 ─┼─► HAProxy:443 ───────┼──► LAN: 0.0.0.0:443 ─┼─┼─► nginx/php │ │
WAN: 0.0.0.0:80 ──┼─► acme.sh:80 │ │ │ │ │ │
└──────────────────────┘ │ │ └─► jail/pgsql │ │
│ │ postgresql │ │
│ └─────────────────────┘ │
└─────────────────────────┘Let's Encrypt Certificates
OPNsense is able to create and automatically renew Let's Encrypt certificates with the ACME client plugin (os-acme-client). The huge advantage is that we have centralised certificate management, do not need to laboriously manage the certificates on each internal target system, and do not need to configure NAT or other firewall settings.
The basic settings described here are sufficient with the following definitions:
- EXTERNHOSTNAME = The externally accessible host name (e.g. nextcloud.domain.de)
- EMAIL = Email address of the Let's Encrypt account (e.g. name@domain.de)
HAProxy
HAProxy receives external requests for port 443, encrypts the connection and then forwards it to the internal Nextcloud server on port 443.
The nice thing is that multiple services can be provided simultaneously on port 443. The difference is made via the external host name called up.
This makes it possible, for example, to forward https://nextcloud.domain.de to Nextcloud and https://domain.de to the actual website, even though both actually require port 443 on the same external IP address.
Here you can also go through this article with the following definitions:
- EXTERNHOSTNAME = The externally accessible hostname (e.g. nextcloud.domain.de)
- IP = IP address of the local Nextcloud server (e.g. 192.168.1.102)
- NEXTCLOUDHOSTNAME = Host name of the local Nextcloud server (e.g. nextcloud.domain.de)
- PORT = Port of the local Nextcloud server (443)
Voilá