Introduction
Attention, this article refers to TrueNAS CORE, which I am now archiving here and for which there are no more updates. Continue with a normal FreeBSD as server with Bastille as jail management.
All articles here are based on the creation of a jail, as I always run each application in its own environment. This ensures clean requirements and no unnecessary mutual dependencies. Jails can run services very simply, leanly and securely. For FreeBSD, it doesn't matter whether one or 100 jails are running at the same time, only the services running in them are relevant. This can be done conveniently via the TrueNAS administration website or directly on the console.
The administration in TrueNAS is managed with iocage and is preinstalled, but can also be installed and used in FreeBSD with pkg install iocage. The advantage is that either via the TrueNAS GUI or a pure shell the most important settings and adjustments can be made. We also do here for both.
Goals
Creation of a jail with the most important basic settings so that other articles can build on it.
NEW: For the very impatient I have a console only section. There are only commands, no explanations.
Last update:
- 10.11.2024: Article archived
- 02.03.2024: Initial version
TrueNAS
The first step is to create a jail on the TrueNAS. To do this, we first open the TrueNAS administration website.
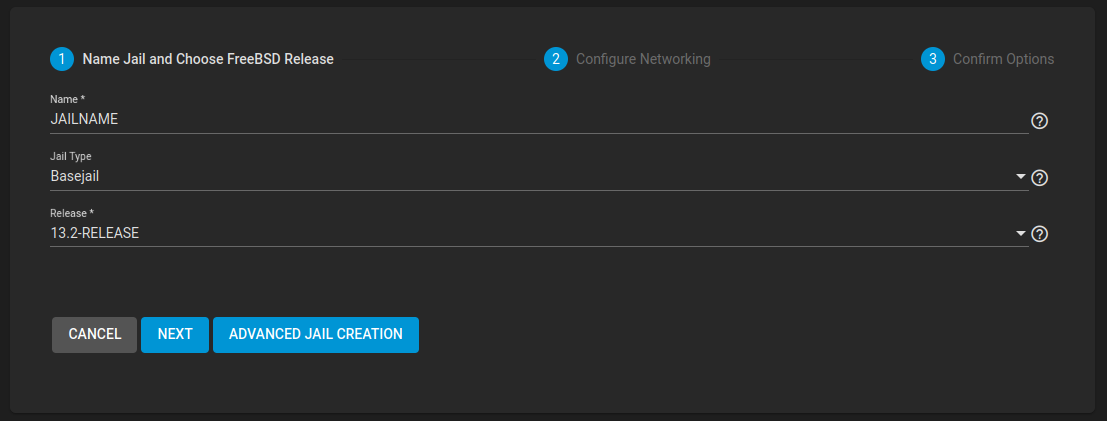
Create
TrueNAS / Jail / Add- Name:
JAILNAME - Jail Type:
Basejail - Release:
13.X - DHCP Autoconfigure IPv4:
Ja - VNET:
Ja
- Name:
Modify
Some services (such as PostgreSQL) require some more specific options. If not, this can be skipped.
- `TrueNAS / Jails / JAILNAME / Edit / Jail Properies
allow_sysvipc= On
Set up user
The webshell in TrueNAS is not suitable for making complex configurations, so SSH is activated.
- Start jail:
TrueNAS / Jails / JAILNAME / Start - Open jail shell:
TrueNAS / Jails / JAILNAME / Shell- Set the
rootpassword withpasswd - Add a user with
adduser USERNAMEImportant: Assign to the groupwheelso that rights can be obtained withsu
- Set the
#Username: USERNAME
#Full name: USERNAME
#Uid (Leave empty for default):
#Login group [USERNAME]:
#Login group is USERNAME. Invite USERNAME into other groups? []: wheel
#Login class [default]:
#Shell (sh csh tcsh nologin) [sh]: tcsh
#Home directory [/home/USERNAME]:
#Home directory permissions (Leave empty for default):
#Use password-based authentication? [yes]Enable SSH
service sshd enableactivates the SSH serviceservice sshd startstarts the SSH serviceifconfigshows the current IPv4 address
It is best to store the IP address statically in the DHCP server so that it no longer changes and publish it via DNS (JAILNAME.domain.local).
Console
iocage create -b -n JAILNAME -r XX.Y-RELEASE vnet="on" bpf="on" dhcp="on"
iocage exec -f JAILNAME "pw user add -n USERNAME -c 'FULLNAME' -d /home/USERNAME -G wheel -m -s /bin/sh"
iocage exec JAILNAME "service sshd enable"
iocage exec JAILNAME "service sshd start"Voilá